An information asset is any information or data that has value to the University, institution or owner.
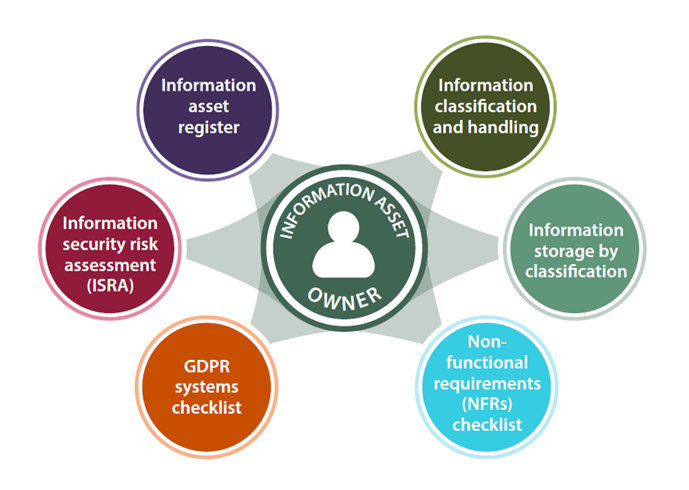
An information asset owner is a person who is responsible for the use of the information asset and ultimately accountable should it be inappropriately disclosed, corrupted or lost.
UIS and the Information and Cyber Security Team have developed various tools for information asset owners to use to ensure that appropriate security is applied to the information asset, in accordance with the impact to the University, Institution or owner should that information be compromised in some way.
The Information Asset Register (IAR)
According to the data protection policy, all information assets containing personal data should be registered in this register. However, we would recommend that all information of value to the University or Institution is registered.
The Information Security Risk Assessment (ISRA)
Once the information assets are registered, or listed, the ISRA 2 form helps the information asset owner (or designee) consider the threats and risks to the information asset, stepping them through a simple methodology to assess the risk. During this process, the owner classifies the information asset and recommended storage locations are suggested. Once the full risk assessment process is completed, the owner should find it easier to decide on the appropriate security controls to implement in order to reduce the risk to an acceptable level.
The Assistive ISRA
The Assistive ISRA is a macro-driven Excel spreadsheet version of the ISRA designed especially for assessing central systems and UAS office systems and processes. It is more open and flexible than the MS Forms ISRA (above) and includes the whole risk management process (listing assets, threats, impacts, controls; risk assessment, risk treatment and risk treatment action plan) but has less guidance built-in. If you would like to use this version of the ISRA it is likely you will need some hand-holding initially. Ask your service manager or relationship manager for more information from the Service Desk. Once you have had the initial introduction/training, you can complete the Assistive ISRA.
Information classification and handling
This page explains who should classify the information asset, how to do it and then where to store it based on the classification.
Information storage by classification
This page gives a set of tables of recommended and not recommended storage solutions for the data, organised by the level of classification.
UK GDPR systems checklist
This is an online checklist to step the information asset owner through various aspects of the system which holds the information asset with regard to how this system is able to fulfil the requirements of the UK GDPR. This, then, only applies to data which is covered by the UK GDPR, i.e. it includes data about a living person and is not fully anonymised. Fully anonymised data (data where it is impossible to associate a specific living individual to any of that data) is exempt from the UK GDPR.
Minimum security requirements for systems and services
This page explains how the minimum security requirements for systems and services help service owners, project and technical leads implement effective security standards for their services. They are known in UIS) as the security non-functional requirements (NFRs) or the security NFRs.
Further information and tools:
Data protection impact assessment (DPIA)
This form helps the information asset owner assess the impact to the data subjects themselves rather than to the University, insitution or the owner, should the data be compromised in some way. It's available from the Information Compliance Office, which would also be able to help with any queries on how to complete it.